Hello Friends, In our previous tutorial we have discuss about ping sweep, today i will explain you the Trace route or simply routing in windows. I know all you know what is trace route but actually you really don't. Its quite different and its use is also quite different. I know you always tried to understand the output of trace route but not been able to what each line means in trace route. So after reading this you can understand everything quite clearly. Today i am writing my WHITE PAPER ON TRACE ROUTE..So read on..
What is Trace Route?
As the name suggests trace route, means tracing the path, but which path. Actually whenever any user opens any website in his web browser, from him it opens directly but have you ever tried to understand what background processing is going on. How your web browser actually getting to that address. That working of website i will explain on some other day but for now must know to reach to someweb address, our web browser goes to different paths and chooses the best suitable path having the minimum response time.
Trace route is a network based utility which shows the path over the network between two systems and lists all the intermediate routers to get to the final destination. For what purpose trace route is used ? Main purpose of trace route is to fix network problems. This helps you in identifying, while connecting to some network where the connection is actually slowing down, which intermediate router is responsible for that.
Technically trace route is also an ICMP echo based protocol similar to ping.
But its only a primary use, for what else we can use this. As i have already told you how to get an IP address. Now when you do trace route with that IP address what it will show is that which service provider the victim is using means ISP(Internet service provider), this will help you in determining his few basic things like Country, state and sometime more deeper information too. Now how this is going to be helpful for Network forensic experts. Suppose you have made an hacking attempt on some bank or some government or some security concerned website, what they do is that they store an IP address and timestamps of each visitor in their database. Now what network forensic expert will do is that it will trace route your IP address and confirm your ISP and your country( country from which ISP belongs). Now Forensic expert will contact your ISP and provide your IP address and time to ISP and ask him to provide details that at that time this IP was assigned to which person and that how they will get complete address of the hacker and catch him red handed. I hope you got my point why trace route is that much important.
How trace route is done practically?
In windows, trace route is done by using the command tracert in command prompt. You can do it two different ways:
1. To trace route an IP address: This can be of any website or any computer system or of any network.
SYNTAX:
tracert IP(like tracert 127.0.0.1)
2. To trace route websites: When you don't know website's IP address let trace route to translate that address for you.
SYNTAX:
tracert websiteaddress(like tracert www.google.com)
More options:
-d Do not resolve address to host-names
-h (maximum hops) Maximum number of hops to search the target system
-j (host-list) Loose source route along with host-list
-w timeout Wait timeout milliseconds for each reply
Linux trace route has more options available.
Note: you will always get less results in case when you try to trace route an Computer system of any victim. Ahhahhh more precisely you will only get around 3 to 10 entries. Three to Four when firewall of the victim doesn't alter your trace routing and more when firewall blocks ICMP echos.
Note: If you get asterisks(*) after the first entry then it confirms that firewall is playing its part and it doesn't allowing us to trace route the system but still we will be able to get his ISP address and with that we can get his location overview.
Understanding Trace Route:
Below is snapshot of normal trace route output of victim (normal computer):
 |
| Trace route live practical example. |
Lets start from very first Line:
1. Very first line after the tracert shows Host Name and IP address which it got using the reverse DNS(domain name system) look up.
2. Over maximum 30 hops: 30 hops means that traceroute will only route first 30 routes between your system and victim's system. 30 is too much it usually ends in 3 to 15 hops but sometimes it goes deeper based on security and no response(as in our first case when we tries to route 14.97.26.147).
Note: Timings are basically round trip times. There are three round trip times in ping. The round trip times (or RTTs) tell us how long it took a packet to get from me to that system and back again, called the latency between the two systems. By default, three packets are sent to each system along the route, so we get three RTTs.
3. This is the address translation private IP by any one of the services from these ( RIPE, ARIN, APNIC, LACNIC, AfriNIC).
These are the IP address ranges for these private IP's:
10.0.0.0 – 10.255.255.255,
172.16.0.0 – 172.31.255.255,
192.168.0.0 – 192.168.255.255
and 224.0.0.0 - 239.255.255.255 are reserved IP Addresses for private internet use for network address translations of above mentioned services.
4. This means that the target system could not be reached. More accurately, it means that the packets could not make it there and back; they may actually be reaching the target system but encountering problems on the return trip (more on this later). This is possibly due to some kind of problem, but it may also be an intentional block due to a firewall or other security measures, and the block may affect trace route but not actual server connections.
5. If firewall doesn't block remote connections then the result will be like this.
Note: This step provides the ISP(Internet service provider).
Now Understanding trace route for websites:
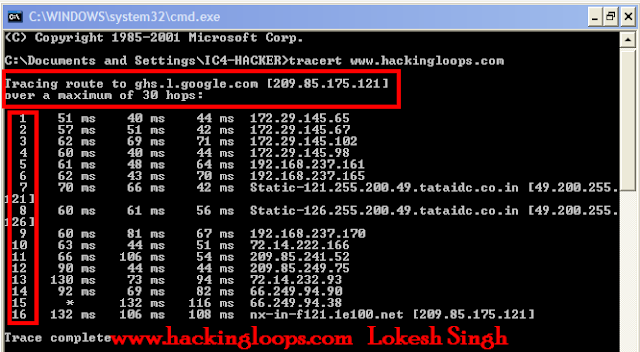 |
| Trace route of website |
Since hackingloops is a blog hosted on google that's why at start it reverse DNS name as ghs.l.google.com and translated IP address of hackingloops is 209.85.175.121. So our destination is 209.85.175.121
Now steps 1 to step 4 shows private internet use addresses as explained above which is used for address translation. Step 5,6 and 9 are also static private IP addresses with which but these are local IP addresses for your localhost with with the DNS communicates.
Step 7 and 8 determines the response from your ISP address. Above clearly predicts i am using tata teleservices ISP.
Step10 and 13, 14 and 15 are also Google IP address responses as this is google blog.
Steps 11 and Step 12 retrieves the different DNS servers of hackingloops.
Step 16 shows our destination..
The above was meaning now lets explain whole process in a go....
First of all my system reverse DNS the IP address of Hackingloops which is found to be 209.85.175.121,Now since i haven't mentioned any specific hop count so by default it considers maximum value as 30 hops. Now my system contacts to IANA service ( RIPE, ARIN, APNIC, LACNIC, AfriNIC) requesting the response from IANA to get the translated address. After a successful query to IANA service it returns the response back to my local system(192.168.***.***) . In between my system also get response from my ISP which is tata teleservices. Now after a successful acknowledgement our system contacts to Google server(72.14.222.166 and 72.14.232.93) which in return returns the DNS server names( for hackingloops and then google confirms the response and returns back the actual web page.













